Introduction
Deck Decoder was a challenge from the 2024 edition of the Midnight Flag CTF. This particular challenge had something to do with your archives getting disorganized and you having to organize them again… Let’s dive in !
The binary
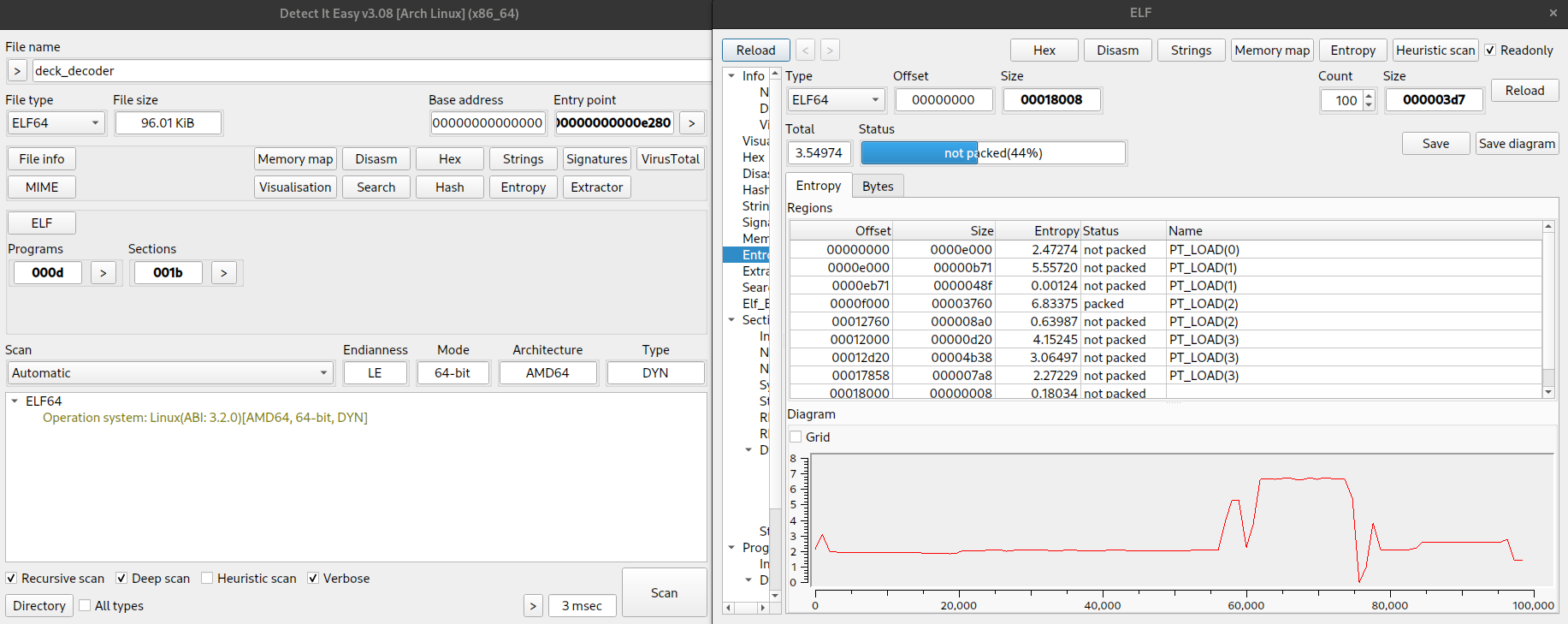
Seems to be nothing special, at first glance we’re dealing with a stripped ELF64 binary, one of the sections seems to have high entropy but nothing too suspicious.
On launch, the code demands a PIN code. After the PIN code it asks for a string. Giving it just any random string will make it print either :( or Uh oh ! stoping here....